Securing Connections in AWS with AWS PrivateLink: A Simple Guide
Introduction
In cloud computing, keeping your data safe and secure is essential, especially when working with sensitive information. AWS offers a service called AWS PrivateLink, which helps you securely connect your Virtual Private Clouds (VPCs) to other AWS services or third-party applications without exposing your data to the public internet.
AWS PrivateLink ensures all communication stays within the AWS network, reducing risks and simplifying your setup. In this guide, we’ll explain how PrivateLink works, its benefits, and how to set it up for your applications.

What Is AWS PrivateLink
AWS PrivateLink provides private connections between VPCs and AWS or third-party services. It uses Interface VPC Endpoints, which function as localized “entry points” in your own VPC. Because traffic never goes over the public internet, your applications gain a stronger security posture.
Key Benefits to using AWS PrivateLink
- Private Access to AWS Services: Connect to services like Amazon S3, DynamoDB, or RDS via private IP addresses.
- Cross-Account & Cross-Region: Easily link multiple VPCs across accounts or geographic regions.
- Third-Party Integrations: Securely connect to SaaS providers that publish an Endpoint Service.
- Microservices-Friendly: Ideal for multi-VPC or multi-account microservices architectures, ensuring data stays private.
General AWS PrivateLink Flow Diagram
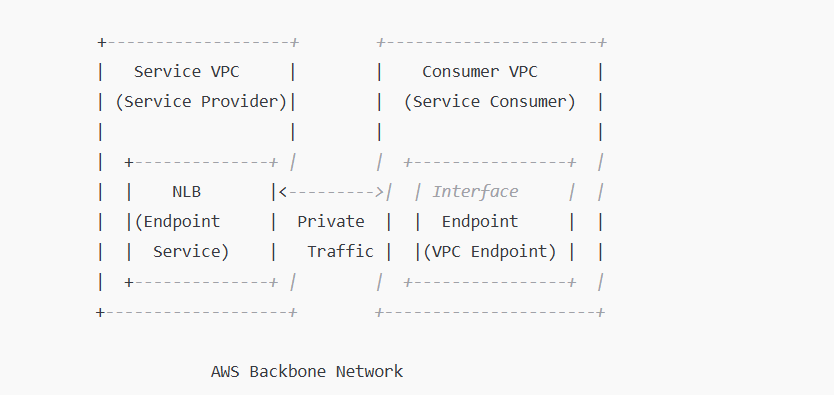
- Service VPC: Hosts the service behind a Network Load Balancer (NLB).
- Consumer VPC: Creates an Interface Endpoint for private communication.
- AWS Backbone Network: Keeps all data within AWS.
Why Use AWS PrivateLink
AWS PrivateLink provides a reliable way to enhance security and reduce complexity in your cloud environment. By leveraging AWS-managed endpoints, you can avoid the need for public IP addresses and internet gateways for certain workloads. Here are some excellent reasons to use AWS PrivateLink:
- Secure Connections
- All traffic remains within the AWS backbone network, minimizing exposure to external threats.
- Excellent for meeting compliance standards such as PCI-DSS, HIPAA, or GDPR.
- Simplicity
- Eliminates the need to manage VPNs, NAT gateways, or external firewalls.
- AWS handles endpoint management, reducing operational overhead.
- Stable IP Addresses
- PrivateLink uses private IP addresses within your VPC, so fewer DNS or IP reconfigurations.
- Consistent connections for smooth communication even as your network changes.
- Scalability
- PrivateLink grows automatically with your workloads.
- Seamlessly integrates with AWS Network Load Balancers (NLBs) for efficient traffic handling.
How AWS PrivateLink Works
Using AWS PrivateLink involves creating Interface Endpoints, setting up security groups, and configuring any necessary listener rules, especially when using a Network Load Balancer. Below is an overview.
- Core Components
- Interface Endpoint (Consumer VPC): A private endpoint that lets you securely access the service.
- Endpoint Service (Provider VPC): Backed by a Network Load Balancer, which your endpoint connects to.
- AWS Backbone: Ensures traffic never leaves Amazon’s internal network.
- Steps to Set Up
- Creating an Interface Endpoint
- In the VPC console, go to Endpoints > Create Endpoint.
- Choose a type of service (AWS, Marketplace, or Private).
- Pick your VPC, subnets, and security groups.
- Creating an Interface Endpoint
- In the VPC console, go to Endpoints > Create Endpoint.
- Choose a type of service (AWS, Marketplace, or Private).
- Pick your VPC, subnets, and security groups.
- Test Connectivity
- Use curl, telnet, or application logs to verify private data flow.
- Creating an Interface Endpoint
- Common Use Cases
- Secure AWS Service Access: Contain traffic to S3, DynamoDB, or RDS within AWS.
- Cross-Region: Link VPCs in different regions securely.
- Third-Party Integrations: SaaS providers offering an Endpoint Service.
- Microservices: Private communication for services across multiple VPCs.
- Internal Shared Services: Provide your custom in-house service (e.g., a shared API or internal tool) with other AWS accounts in your organization via PrivateLink, without exposing it publicly.
Real-world Example: PrivateLink with Oracle GoldenGate
With over twenty years of experience, Apps Associates has helped our customers through some complex challenges. I’d like to share this example of a recent project involving AWS PrivateLink and Oracle GoldenGate. The requirement was to replicate data from an Oracle Database using Oracle GoldenGate, a real-time data integration and replication solution, without exposing traffic publicly.
Here are some key components of this implementation:
- Consumer VPC
- Hosted our Oracle DB & GoldenGate (Extract/Replicate) processes.
- Created an Interface Endpoint specifically for GoldenGate traffic.
- Provider VPC
- Placed the GoldenGate replication target behind a Network Load Balancer.
- Exposed this as an Endpoint Service, which the consumer’s Interface Endpoint could securely connect to.
- AWS Backbone
- All replication data flowed exclusively through AWS’s internal network, avoiding public IPs altogether.
- Result
- Enhanced Security: No traffic touches the public internet.
- Consistent Latency: Private links are often more predictable than public routing.
- Regulatory Compliance: Meets stringent requirements by keeping data strictly private.
- Simplicity: Eliminated complex VPN or NAT setups.
Oracle GoldenGate Integration Flow Diagram 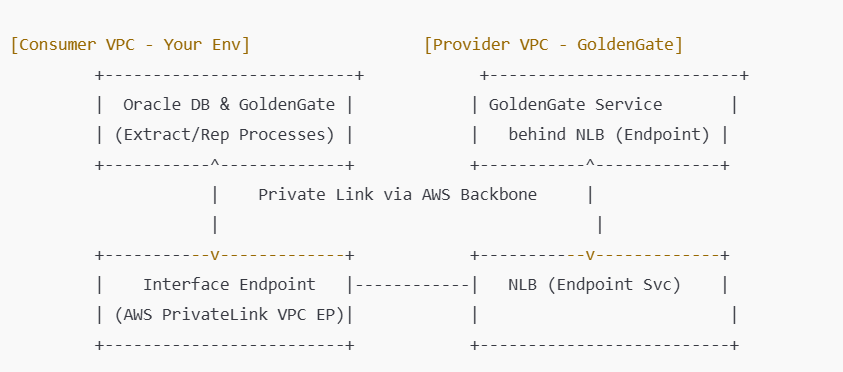 Conclusion
Conclusion
AWS PrivateLink simplifies secure communication in the cloud. By keeping your data within AWS’s network, it ensures security, scalability, and ease of use. Whether accessing AWS services, connecting to third-party providers, or managing microservices, PrivateLink is a reliable solution.
Explore more on AWS PrivateLink to enhance your cloud security from the reference below Learn more: AWS PrivateLink Documentation
